ESET cybersecurity specialists have identified a new malware sample called HybridPetya that can bypass the UEFI Secure Boot mechanism in Windows. According to NotebookCheck, this poses serious concerns.
Typically, UEFI Secure Boot checks the digital signatures of programs loaded during the computer's startup, blocking any unauthorized or malicious code.
HybridPetya can determine if the infected device uses UEFI with GPT, and if so, it bypasses Secure Boot. It then modifies, deletes, or adds files in the boot partition, making it difficult to access other data on the disk and potentially encrypting it.
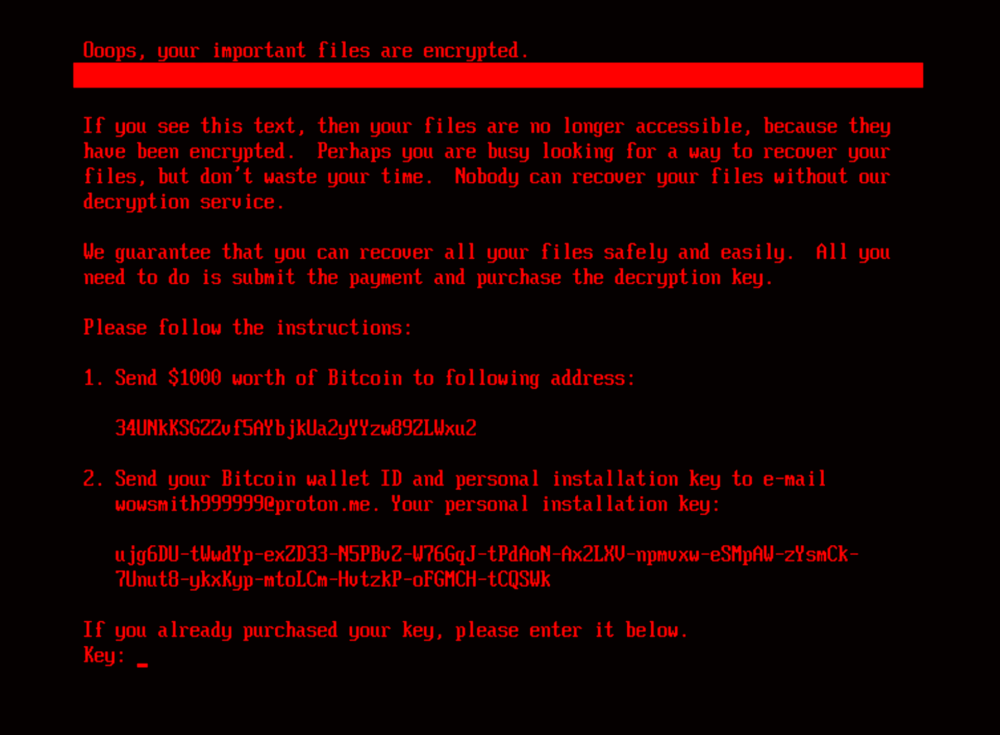
Upon activation, the program displays a message about file encryption and demands a payment of $1000 in bitcoin. It includes the cryptocurrency address for the transfer and instructions to send the wallet address and generated installation key to a ProtonMail email for the decryption key.
As of September 12, 2025, ESET has not recorded any real attacks using HybridPetya. Experts suggest that this sample may be a prototype or in the testing phase before a broader release.
The vulnerability exploited by this malware was patched in the January Windows update (Patch Tuesday, January 2025). Therefore, users who have installed the latest updates are protected from this threat.
It is currently unknown whether HybridPetya can affect other operating systems, such as macOS or Linux.